Compliance
24/7 protection against malware, data breaches, and other cyberattacks
We have solid experience in streamlining technology and ensuring that your business is compliant
Founded in 2014, Uzado is a Canadian-based company, with operations across Canada and the United States. We provide 24/7 Cybersecurity and Compliance Services that align our clients’ goals with their partners and government contractual mandates. We focus on using insights to drive business decisions. Our specialists don’t leave strategies to chance by analyzing data and showing what changes to make, and how to make them. Uzado offers multiple services to help companies simplify IT, centralize Cybersecurity management, and meet compliance standards. We can also customize our services so that we work with your existing IT network and programs.

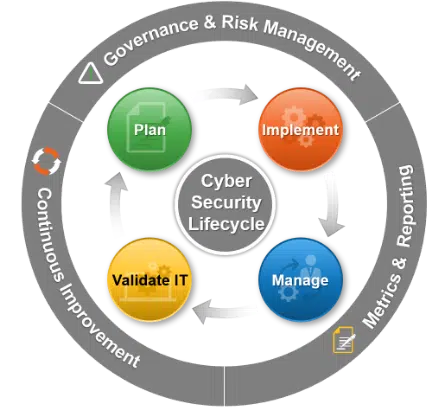
Managing Your Journey with Uzado’s Life Cycle
By understanding the ins and outs of your technology, we can execute the best methodology to constantly improve and fully optimize your systems with data-driven insights. Here’s what happens throughout your journey with Uzado:
Driving business growth with a secure and compliant IT system
At Uzado, we recognize that businesses need to have a well-protected IT infrastructure that meets regulatory standards to stay ahead of the competition. With our expertise in cybersecurity and compliance, your company’s growth potential is limitless.
Recommend Uzado
Uzado takes pride in providing top-tier IT solutions and exceptional service to our clients, and we are committed to giving the same level of service to your contacts. Simply fill up the form for partnership opportunities and we’ll reach out as soon as possible!
